Iron Security is the ultimate WordPress security plugin
Protect your WordPress website from any threat
What is a botnet? Are you still searching for the answer? It is an important aspect of cybersecurity. A botnet is like an open network that is affected by attackers and threats.
If you don’t take necessary steps against these cyber threats, you can end up with compromised computers and infected iot devices.
What is a Botnet? Understanding the Botnet Definition
The botnet definition is simple to understand: it is a network of connected devices that are affected by any kind of malicious software and are under the full control of the cybercriminals. These compromised computers or devices on the network are called zombie computers or “bots.” These zombie computers can execute malicious codes without the permission of the owner.
Botnet resembles how these automated systems work together while being controlled from a central location. It’s difficult to create these botnets; cybercriminals tend to use large-scale computing powers and the necessity of bandwidth through multiple devices. These requirements are important to launch large-scale attacks.
How Botnets Work: The Study of Digital Zombies
If you want to know how botnets work, you first need to understand their complex infrastructure. Here is how botnets operate: they go through a system of infected computers where they get remote commands from cybercriminals who are the bot herder controllers. A bot herder is a digital or online criminal who has control over the botnet.
The bot herder is responsible for sending remote commands that run malicious activities on infected systems. Let’s understand how botnets really work. You must understand these processes, which include these key stages:
What are the types of botnets?
Centralized Botnets
Centralized botnets follow the client-server model, where they work like a team. Here the infected computers talk to one main computer known as the central server. This model is easy to manage as a botnet controlled by a bot herder.
Although centralized botnets operate on the dark web, enforcement agencies can identify the main servers and shut them down.
Peer-to-Peer (P2P) Botnets
Peer to peer botnets are networks of computers that are already infected. This botnet is unique in its own way because infected devices in the network can communicate with each other without the need for a host server. In addition to this, P2P botnets have the capability to operate even if each is removed by security teams from legal authorities.
The main advantage of this botnet over centralized botnets is that injected computers don’t rely on a central server for communication.
List of Common Botnet Attacks and Their Impact
DDoS Attacks: Overwhelming Digital Infrastructure
DDoS attacks, or Distributed Denial of Service attacks, are one of the common ways one utilizes the botnets. The DDoS attack uses the collection of thousands of infected devices that work together to perform attacks on the target system. This attack is a threat to online businesses because it disturbs the operation of the system for hours or, in the worst case, for weeks.
Here are some ways these botnet attacks can perform the following actions:
- Stop business operations for days or hours.
- Cause users to lose a lot of money.
- Trust in the company and its reputation will be hurt.
- Use it as cover for other malicious tasks to happen.
Data Theft and Credential Harvesting
Botnets are modern malware that are best at easily stealing the important data and information from their target, which is user computers. This sensitive information can be login credentials, financial data, or any other personal information. Cybercriminals, or bot herders, usually use the infected computers to steal away the data and collect important login information from many users within a short period of time.
This information is high in value, as it can be sold through encrypted websites. This is the reason we see many cybercriminal activities and identity theft with a sole reason to sell these information for high price.
Cryptocurrency Mining and Click Fraud
In today’s technologically advanced world, botnets tend to use the target devices for cryptojacking. Cryptojacking is a process of using the hacked or compromised device to secretly mine cryptocurrency. All the work starts without any knowledge or permission from the user or victims. Advertisement fraud or spam campaigns are some ways attackers make money using several users computers.
Spam Distribution and Email Campaigns
Botnet infections are harmful, as they can carry out large-scale spam distribution operations. These infected computers tend to spread large numbers of spam emails or spam campaigns to legitimate users. These emails contain suspicious links that carry malicious code in them.
The Rise of IoT Botnets: New Cyber Threats
IoT, or the Internet of Things, is the network of physical devices that use sensors and software. Some of the widely known IoT devices are cameras, routers, smart lights, smartwatches, and so on. These devices are widely used and have weak security. This is the reason why attackers target them for botnet infections. They lack necessary security measures, which makes them attackers’ favorite target devices. IoT botnets are vulnerable because many users never change their default passwords.
One of the prime examples is the Zeus botnet, which is a famous network of hacked computers. These computers are used for stealing data. This Zeus botnet has already shown how dangerous these attacks are, especially when launched in huge DDoS attacks with hacked smart devices.
Challenges with IoT Botnet Detection
As we all know, IoT devices are widely used; this makes it harder for security teams and agencies to identify these botnet infections in vulnerable systems. Along with this, there are many different challenges with IoT botnet detection:
- Not enough processing power for anti-virus software
- Manufacturers don’t release security updates very often.
- Monitoring network traffic from many small devices is hard.
- Users aren’t aware of the security risks and botnet presence in IoT.
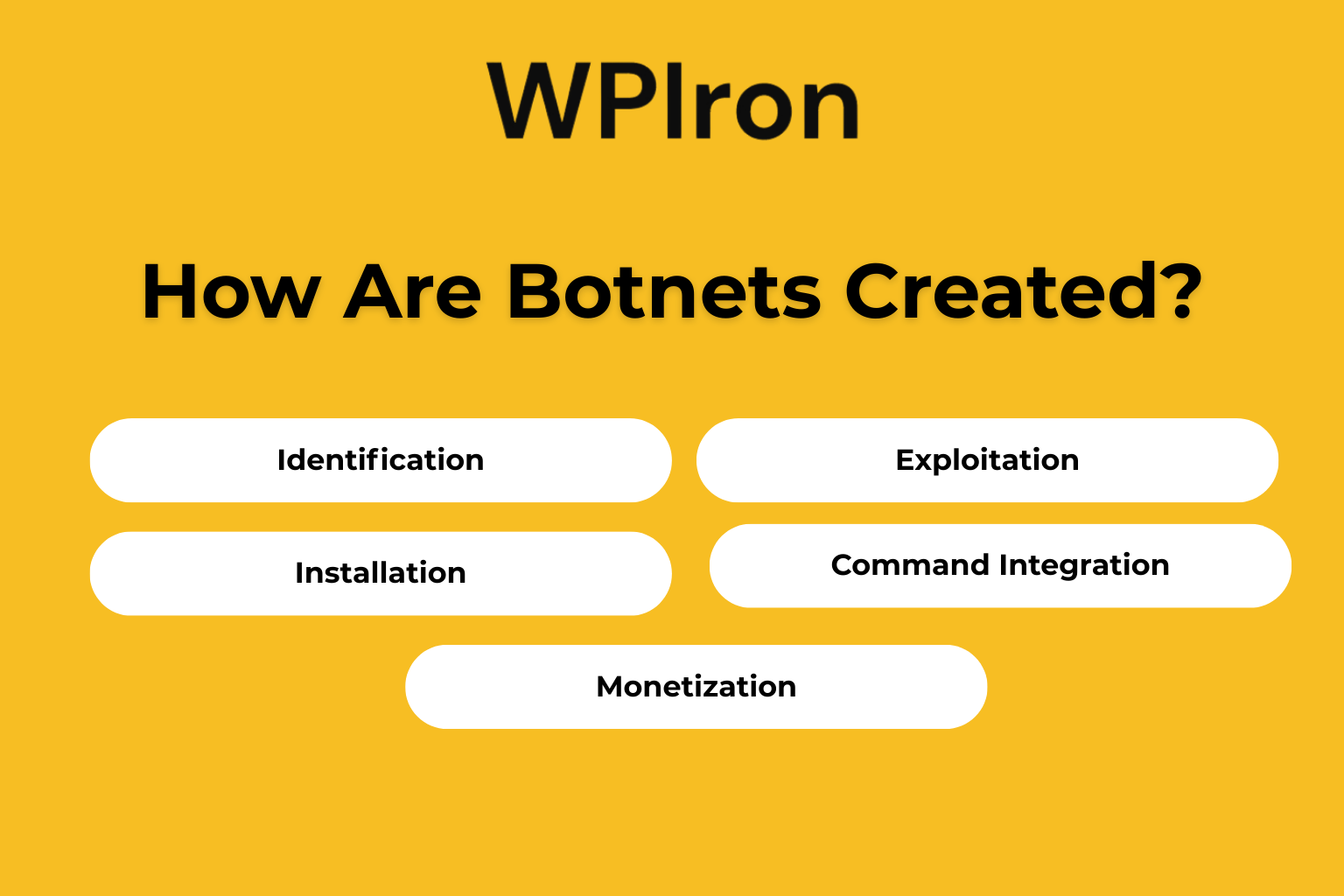
Botnets were created by cybercriminals using systematic campaigns to target vulnerable systems on the network. The botnet creation involves the following process:
- Identification: Identifying infected systems and target devices with software vulnerabilities
- Exploitation: Using malware distribution, phishing attacks, brute force attack methods, or technical exploits
- Installation: Deploying botnet malware on computers and mobile devices with weak security measures.
- Command Integration: Connecting infected devices to C&C infrastructure so bots can connect to the network.
- Monetization: Leveraging the entire botnet for profitable criminal activities.
How to Prevent Botnet Attacks
We have gathered ways to stay safe from botnet threats. We have broken them into individual protection strategies and organizational defense measures:
Individual Protection Strategies
To prevent botnet attacks and protect users computers from becoming part of infected machines networks:
- You need to fix your software vulnerabilities. This can be done by keeping your operating systems and software regularly updated.
- You should always use anti- virus software with a real-time feature.
- You should avoid clinking on spam links and never download malicious files from internet.
- As an individual, develop a habit to timely change your password on your IoT devices.
- Learn to monitor your network traffic and keep track of unusual activities.
- Never open unknown emails, as they could be infected with spam emails or contain phishing attacks.
Organizational Defense Measures
As an organization, they must make an extra effort in preventing the botnet attacks. All the security agencies in the organization should implement these defense measures:
- Make use of endpoint detection and response solutions for all the computer systems.
- Make users aware of cybersecurity and ways to stay safe from phishing attacks and suspicious links.
- Network segmentation is a great strategy that can be used to limit the injection of these botnet attacks.
- It’s crucial to monitor and keep track of the system’s performance or security status. botnet presence in network traffic.
Conclusion
Understanding what is a botnet in cyber security is essential in our increasingly connected world. These networks of infected devices pose significant risks to individuals, businesses, and critical infrastructure. Botnet attacks continue to evolve, with cyber criminals developing new methods to recruit infected machines and perform attacks against legitimate users.
By maintaining strong cybersecurity practices, staying informed about emerging cyber threats, and implementing comprehensive security measures, we can better defend against botnet attacks and protect our digital assets. Security agencies must remain vigilant against malware distribution, phishing attacks, and other techniques used for botnet recruitment.
The fight against botnets requires ongoing vigilance from users, organizations, and enforcement agencies working together to identify threats, share intelligence, and develop effective countermeasures. As cyber threats continue to evolve, our understanding and defensive strategies must evolve as well to stay safe from botnet attacks and protect different devices from becoming part of these criminal networks.

Iron Security is the ultimate WordPress security plugin
Protect your WordPress website from any threat
Botnet FAQs
How do peer to peer botnets differ from centralized control?
Peer to peer botnets let infected machines talk to each other directly, while centralized control uses a single server that bots contact for commands.
What are IRC botnets?
IRC botnets use Internet Relay Chat channels as their command-and-control channel so bots can connect and receive instructions through IRC servers.
What is a zombie computer?
While the technology itself isn’t inherently illegal, using botnets for unauthorized activities like DDoS attacks, data theft, spam distribution, or ad fraud is criminal in most jurisdictions worldwide. Law enforcement agencies actively pursue cybercriminals operating these networks.
Can mobile devices be infected by botnets?
Yes, mobile devices can become part of botnets through malicious apps or malicious download activities. Mobile botnets targeting mobile devices are increasingly common as smartphone usage grows.
Do botnets cause data breaches or steal sensitive data?
Yes, some botnets are designed to steal sensitive data (credentials, financial info), which can lead to large data breaches.
How are IP addresses and bots connect used in tracking or hiding botnets?
Bots connect using many IP addresses (often distributed), which makes tracking harder; threat actors may also rotate IPs or use proxies to hide control channels.